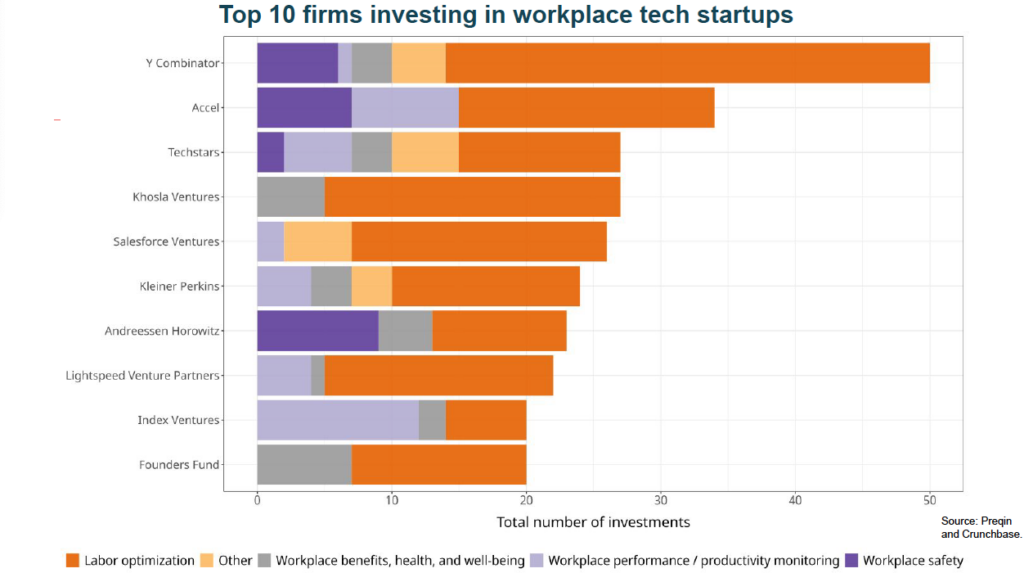
Over the last decade, Big Tech companies have transformed the world economy and taken the driver’s seat in international markets. Meanwhile, new startups are constantly emerging, often turning into “unicorns” backed by private capital — companies worth billions of dollars that are not held to any reasonable standard of public accountability. In many cases, the applications of these companies’ powerful technologies are detrimental to human rights, climate, and the environment, not to mention democracy itself.
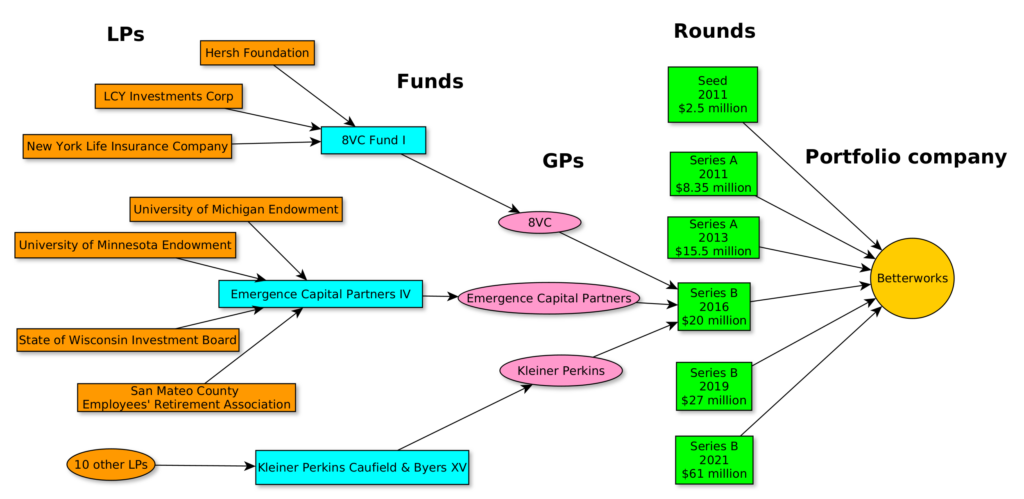
Select investment flows: Betterworks
At Empower, we research the political, social, and environmental consequences of this new regime – technofeudalism – including government and private-sector usage of their products. For example, governments actively participate in the development of surveillance technologies through public contracting by military, police, immigration, and health agencies, among others. More recently, the investment boom in artificial intelligence (AI) has sharpened our focus on the myriad threats it poses.
Our work has covered topics such as:
- Private-sector data brokers selling personal information en masse to immigration authorities for purposes of planning raids and targeting individuals.
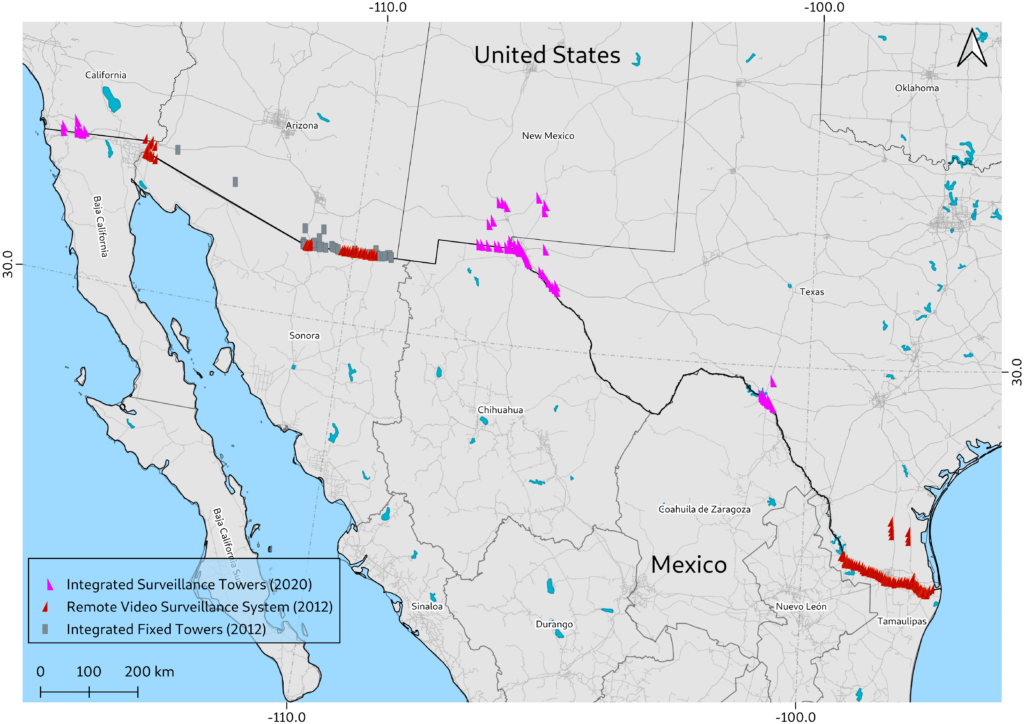
- “Digital border” surveillance tools such as drones, thermal sensors, intelligent camera systems, cell phone hacking tools, and integrated tower systems.
- Collection and analysis of biometric data, using facial recognition and similar techniques, including access to social networks.
- “Bossware” that employers use to automate hiring decisions, spy on employees, and optimize labor productivity at the expense of workers’ rights.
- Military applications of AI such as autonomous weapons systems and data analytics.
- Tracing financial flows to Generative AI startups, from passive institutional investors to venture capital and private equity firms.
- Explosive growth of data centers to support AI that strains energy grids, drying up the water supply in arid regions across the globe, and drives a new boom in fossil fuel extraction and infrastructure.
- Corporate capture of political actors in Washington DC and elsewhere by the “tech broligarchy,” seen in revolving door practices, lobbying, and campaign contributions.
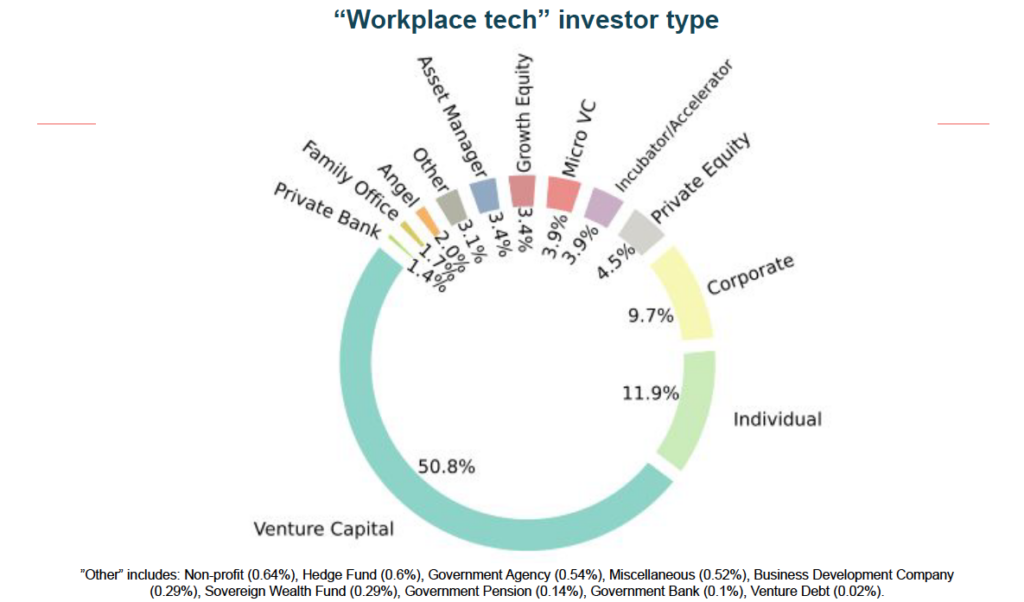
Our methods
Strategic research on tech companies tracking beneficial ownership, financing, and business partners, with extensive knowledge of public sources and access to proprietary trade and financial databases.
Building databases, maps, and visualizations for tailored analysis of complex financial flows.
Public information requests to obtain technical documents and relevant communications between governments and private contractors.
Monitor legislation and public policies that regulate the use of new platforms and databases, including inter-agency and bilateral agreements that facilitate the sharing of personally identifiable information.
U.S.-Mexico border surveillance tower installations
Tracking project development of major AI and cloud infrastructure, from energy and water usage agreements to tax breaks, subsidies, and regulatory approvals.
Analysis of public procurement for surveillance technologies, weapons systems, cloud services, and other products.
Legal research to keep up with regulatory and commercial disputes.
Analysis of lobbying and campaign finance to identify conflicts of interest and revolving door practices.
AI foundation model development by metro area
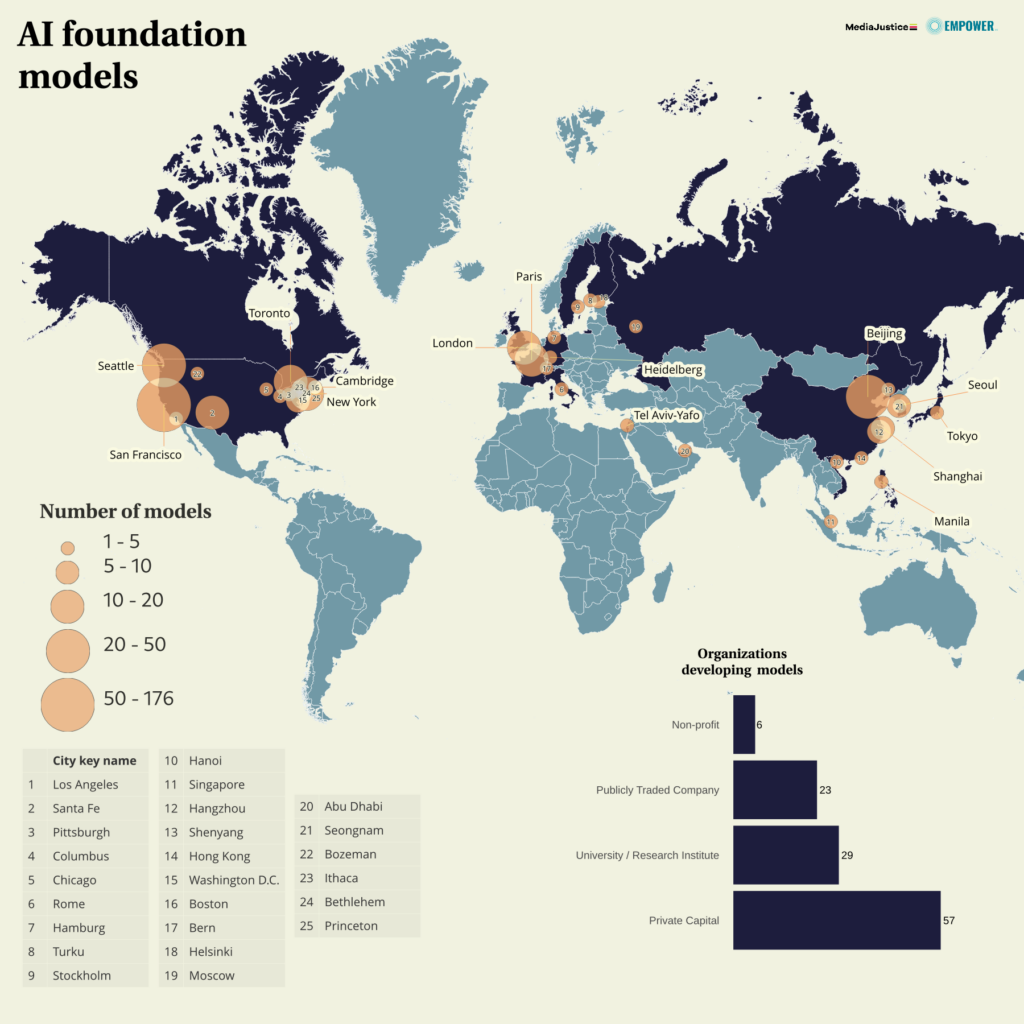
Examples of our work
Our diverse, globaly array of clients and counterparts uses our research for public-facing reports, investor engagement, and campaign materials, for example in the areas of technology and immigrant rights, surveillance, artificial intelligence, corporate capture, and financial flows, including:
- Who’s Behind ICE? The Tech and Data Companies Fueling Deportations (National Immigration Project, Immigrant Defense Project, Mijente)
- The War Against Immigrants: Trump’s Tech Tools Powered by Palantir (Mijente)
- The Deadly Digital Border Wall (Mijente, Just Futures Law, No Border Wall Coalition)
- Sabotaging Sanctuary: How Data Brokers Give ICE Backdoor Access to Colorado’s Data and Jails (Mijente, Colorado Immigrant Rights Coalition, Just Futures Law, The Meyer Law Office, ACLU CO, Denver Justice Project, American Friends Service Committee Colorado, Denver Justice and Peace Committee (DJPC), Colorado Consumer Health Initiative, Colorado Jobs with Justice, Accompaniment & Sanctuary Coalition Colorado Springs, Grupo Esperanza de Colorado Springs)
- Subjected to Surveillance: ICE Access to New Mexico Residents’ Personal Data (Somos Un Pueblo Unido, Just Futures Law, Mijente)
- HART Attack: How DHS’s massive biometrics database will supercharge surveillance and threaten rights (Mijente, Just Futures Law, Immigrant Defense Project)
- Automating Deportation: The Artificial Intelligence Behind the Department of Homeland Security’s Immigration Enforcement Regime (Just Futures Law, Mijente)
- ICE Digital Prisons: The Expansion of Mass Surveillance as ICE’s Alternative to Detention (Just Futures Law, Mijente)
- Divesting for Immigrant Justice (American Friends Service Committee)
- A Human Rights Impact Assessment of Microsoft’s Enterprise Cloud and AI Technologies Licensed to U.S. Law Enforcement Agencies (Foley Hoag)
- WTF: The Rise of the Boligarchy Political Education Series (MediaJustice)